South24 Compilations
10-07-2024 at 8 PM Aden Time
Aden (South24)
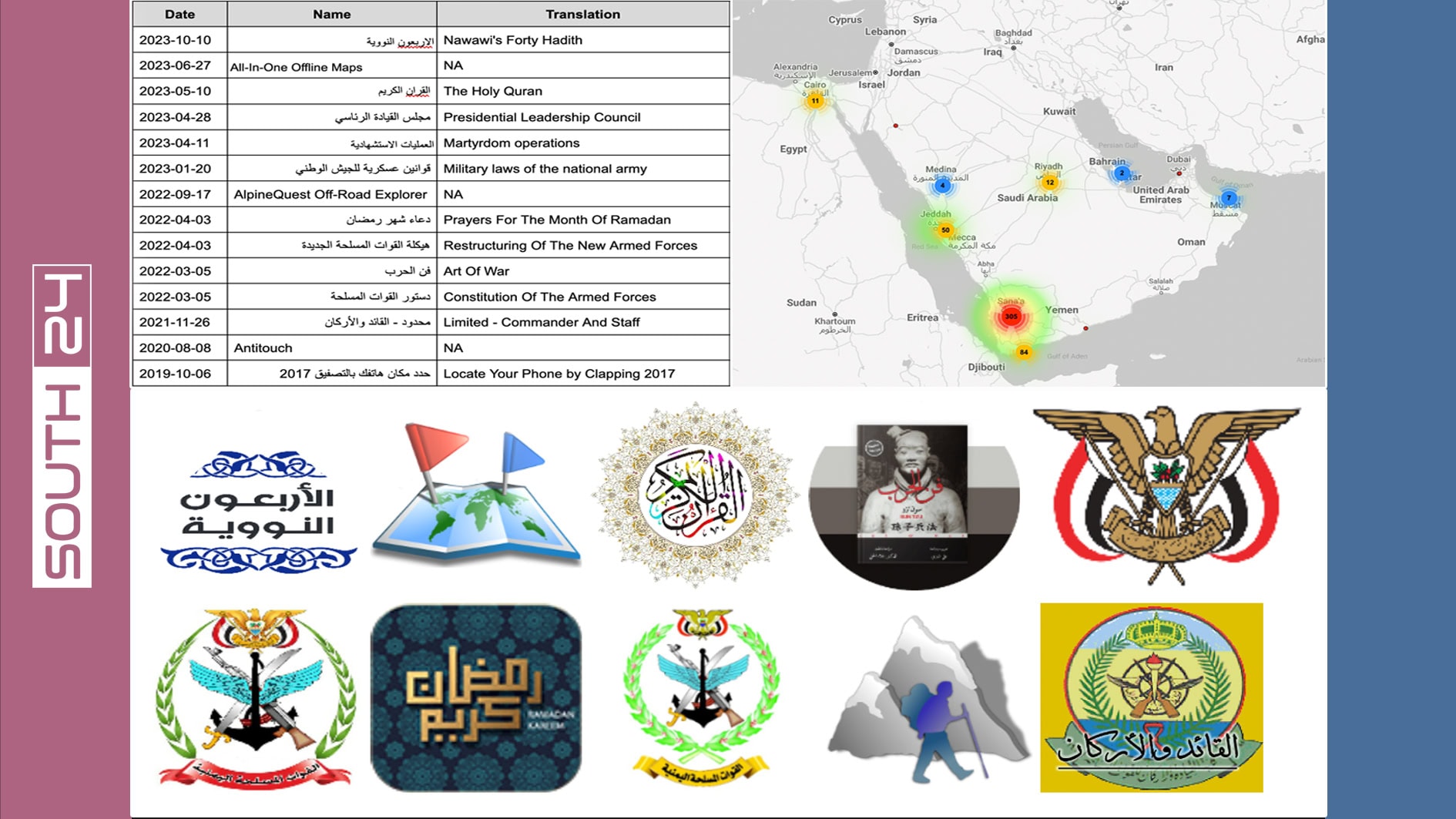
The American cybersecurity company Lookout revealed that the Houthis are using surveillance software to eavesdrop on military phones in the Middle East, targeting more than 450 IP addresses belonging to people in Yemen, Saudi Arabia, the UAE, Egypt, Turkey, and Qatar.
In a report published yesterday, Lookout said that a Yemeni hacking group affiliated with the Houthis targeted the phones of Middle Eastern military personnel with surveillanceware, highlighting how phone monitoring is used in global conflicts.
The report indicated that the Houthi-aligned hackers have succeeded in installing surveillance programs since around October 2019, targeting military personnel they deemed important. The report revealed that the malware, known as "GuardZoo," can collect phone data including the device’s location, photos, documents, and data files related to specific locations.
According to the report’s analysis of server logs observed in a single day, 88 victim devices were located in Yemen, 14 in Saudi Arabia, five in Egypt, two in the UAE, and one each in Turkey, Qatar, and Oman.
Lookout’s analysis also indicated that the spyware had infected devices belonging to military forces of Yemen’s internationally recognized government, located temporarily in Aden.
The Yemeni group’s campaign mostly uses military themes to attract victims, but Lookout investigators also noted that religion and other themes are used, citing examples such as the religious-themed "Prayer" app, and an e-book-themed lure.
The GuardZoo program is a modified version of the "Dendroid RAT" spyware that leaked online in 2014, with new functions added by the Yemeni hackers to collect data from target phones.
“This shows how the mobile phone has truly become a cyber target in every conflict on Earth,” said Christoph Hebeisen, director of security intelligence research at Lookout, adding that the Houthis were able to create this type of cyber weapon despite limited resources.
The report explained that the Houthis used cyber capabilities to implement a digital espionage campaign that lured in and infected targets via WhatsApp, WhatsApp Business, and browser download. Lookout's security intelligence engineer, Alemdar Islamoglu, added that the group was particularly interested in maps that might reveal the locations of military assets.
Lookout also reported these findings to Google, who confirmed that no applications containing the malware are currently detected on the Google Play Store.
Since 2015, the Houthis have controlled the internet and communications services that most Yemenis rely on. It’s believed the Iran-backed militant group uses communication technology to spy on opponents and launch attacks, as well as enjoying significant financial benefits from it.
South24 Center